The Stuxnet and Target attacks have squashed many of the myths about securing industrial control system security.
Wait, you don’t know about Stuxnet and Target?
- The Stuxnet Worm, first discovered in 2010, was responsible for damaging approximately 1/5th of the centrifuges in Iran’s nuclear program. The complex malware exploited four zero-day vulnerabilities, and eventually targeted specific programmable logic controllers (PLCs) and supervisory control and data acquisition (SCADA) computers.
- In 2013, Target’s in-store point-of-sale devices were infected by memory-scraping-malware, which allowed hackers to capture the data stored on magnetic strips of credit/debit cards as they were swiped. The hackers infiltrated Target’s internal systems using the stolen credentials of a third-party HVAC contractor, obtained through an email phishing attack, which also gave them direct access to Target’s payment system.
Myths Surrounding Industrial Control System Security:
Myth #1 – Isolating control systems networks keeps them safe from malicious attacks: FALSE.
In the Stuxnet attack, the SCADA systems and PLCs that controlled the Iranian nuclear centrifuges were air-gapped, theoretically isolating them from the public internet. It is widely believed that the Stuxnet worm was implanted using admin credentials and USB thumb drives on the internal air-gapped computers.
Myth #2 – Highly specialized controllers and industrial control networks are safe from attack due to “security through obscurity”: FALSE.
The Target attackers used custom malware that was unrecognizable by standard anti-virus software, and exploited a previously unknown flaw (a.k.a. zero-day vulnerability) in what was then traditional retailer point-of-sale encryption.
The Stuxnet worm was constructed to look for specific PLC’s, software, and industrial devices. If the worm infected a host computer and did not find the specific systems, it would move on to the next machine, and erase any evidence of itself upon departure.
Myth #3 – Firewalls, Intrusion Detection Systems (IDSs), and Intrusion Prevention Systems (IPSs) effectively protect control system networks from attack: FALSE.
ICS networks are subject to man-in-the-middle attacks, where the hackers capture control system protocol messages that are sent in plaintext in TCP packets.
Once the attackers figure out what is going on, which can take some time and/or knowledge of the industrial process, they can replace the intended plaintext commands with malicious commands that can cause damage.
The firewalls and IDS/IPS system don’t recognize the altered packets as malicious, because they appear to originate from an authorized host, and look like typical control system protocols. Target’s security team received alerts from their Intrusion Detection System, but basically ignored them.
Design with Least Privilege & Least Route
To minimize the chances and impact of an attack on a control system, AV programmers and system designers should employ the principles of Least Privilege (or Use) and Least Route for better industrial control system security.
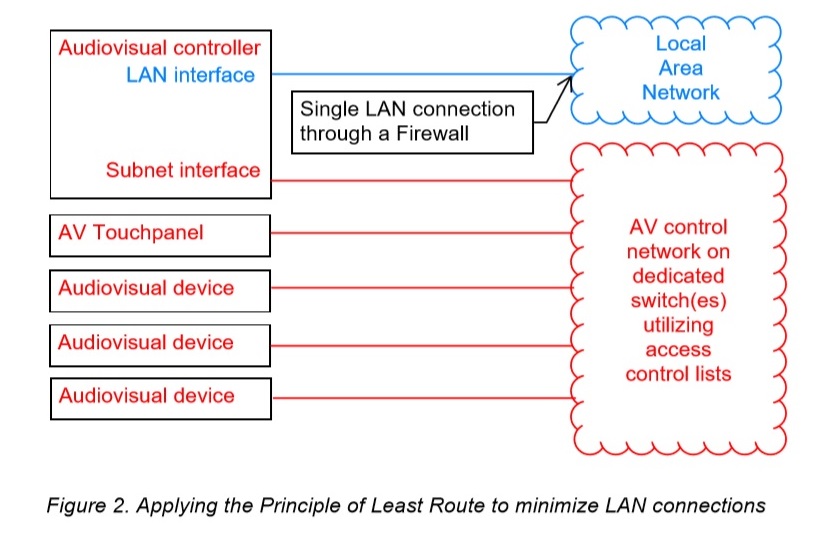
Least Privilege means that users or services should only be given the minimum access required to do their job. Similarly, the principle of Least Route states that a device should only possess the minimum level of network access that is required for its individual function. [related]
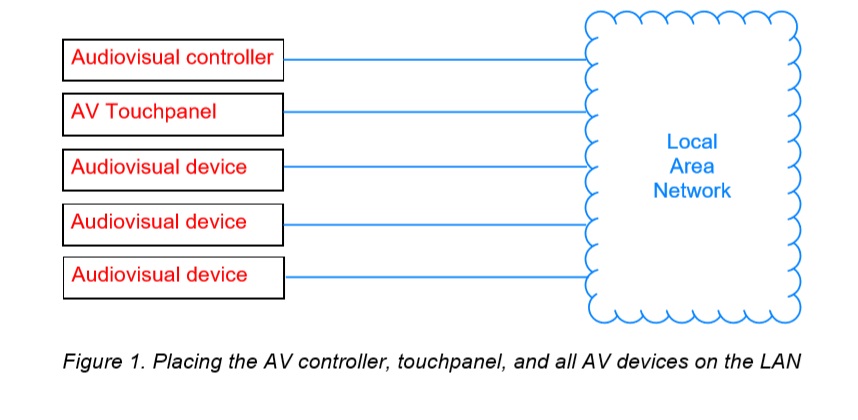
Instead of placing AV devices on open, general-purpose local area networks, AV devices should be placed on their own dedicated, purpose-built networks.
The network switches and routers should be configured using access control lists (ACLs) so that only specific, authorized devices can send traffic inside or outside of the network. VLANs are not an effective security measure.
Air-gapping AV control systems certainly makes them safer, but not completely, and many AV devices are now constantly monitored by internal support staff and/or external AV integrators.
This does not mean that everything in industrial control system security needs to be on the local area network. Many AV controllers have dual network interfaces that allow the AV devices to be placed on a dedicated control subnet, and the AV controller can communicate to the supervisors using the second networks interface via firewall.
This is a good example of Least Route. Technically speaking, network traffic can traverse the two network jacks, but it is difficult.