As if integrators don’t have enough to worry about when it comes to installing new technologies for clients, they have to worry about the omnipresent threat of cyberattacks as well.
Cyberattacks have been on the rise in recent years and have only been exacerbated by the COVID-19 pandemic. A recent study from HP determined global cyberattacks have risen 238% since the onset of the pandemic.
“As the lines between work and home have blurred, security risks have soared and everyday actions such as opening an attachment can have serious consequences,” said Joanna Burkey, chief information security officer (CISO), HP Inc. “Without all of the pre-pandemic sources of visibility of devices, and how they are being used and by who, IT and security teams are working with clouded vision.”
This particular sentiment can clearly be applied to many K-12 and college students in 2020 and 2021 as most were learning remotely at some point, relying on technology for their education and making them prime targets. In the 2020 calendar year, there was a record-breaking 408 publicly-disclosed cybersecurity incidents at K-12 schools, according to the K-12 Security Information Exchange. In the last year, there were 1,332 cybersecurity incidents at educational institutions, says Verizon’s 2021 Data Breach Investigations Report.
As for healthcare organizations in the U.S., according to a Dec. 2020 report, more than 90% reported at least one cybersecurity breach over the last three years. In 2020, the average cost of a data breach in the healthcare industry hit $7.13 million — 84% more than the global average of $3.86 million.
Overall, cybersecurity is extremely complex, and along with that complexity comes a plethora of terminologies. For someone not involved in day-to-day cybersecurity activities or who may be new to the industry, these terms can be overwhelming. Because of this, we thought it would be helpful to pull together an overview of terms you’ll see or hear when engaging in cybersecurity content or discussions, and the differences between the most common types of cyberattacks.
We’ll also provide some information on how different types of cyberattacks are continuing to affect K-12, higher education, and healthcare campuses.
General Cybersecurity Terms
- IP address: Each computer has a unique Internet Protocol (IP) address, which consists of a set of numbers. The set of numbers is a language that computers use to communicate with each other over a network. IP addresses allow any number of internet-connected computers to be distinguished from other computers. Blue Host compares it to calling someone on the phone — everyone has a unique phone number, and you have to dial that number to reach someone.
- Domain: A group of computers, printers and devices that are interconnected and governed as a whole. In layman’s terms, a domain name is the text that a user types into a browser window to reach a certain website.
- Domain Name System (DNS): Domain Name System (DNS) converts human-readable domain names, such as www.google.com, to machine-readable IP addresses. When you go to your web browser and type in a domain name, it will connect with the DNS. The DNS then searches through all of the registered IP addresses and connects that domain name with the IP address. Continuing with the phone analogy, Blue Host compares domain names to contacts in your phone — instead of typing in the full phone number to call someone, you click on the contact’s name.
- Virtual Private Network (VPN): A tool that allows users to remain anonymous while using the internet by masking the location and encrypting traffic. It allows private networks to send data across shared or public networks as if their devices were directly connected to a private network.
- Firewall: A network security device that monitors incoming and outgoing network traffic and allows or blocks data packets based on a set of security rules. Its purpose is to block malicious traffic.
- Cloud: Technology that allows for the access of files and/or services through the internet from anywhere in the world. It is a collection of computers with large storage capabilities that remotely serve requests.
- Spyware: Software that is installed on a device without the end user’s knowledge and spies on their activity. It can invade the device, steal sensitive information and internet usage data, and relay it to advertisers, data firms or external users.
- Trojan: A type of malicious software that downloads onto a computer disguised as a legitimate program. It is a type of malicious software that typically gets hidden as an attachment in an email or a downloadable file and then transfers onto the user’s device. Unlike computer viruses or worms, a Trojan does not self-replicate, so it needs to be installed by a valid user.
- Virus: A type of malicious code or program written to alter the way a computer operates and is designed to spread from one computer to another.
- Worm: A type of malicious software that spreads copies of itself from computer to computer. It can replicate itself without human interaction and does not need to attach itself to a software program in order to cause damage. The primary difference between a virus and a worm is that viruses must be triggered by the activation of their host while worms are stand-alone programs that can self-replicate.
- Bot/Botnet: A type of software application that performs tasks on command, allowing an attacker to take complete remote control of an affected device.
- Encryption: The process of converting human-readable plaintext to incomprehensible text to prevent theft. It is a way of scrambling data so only authorized parties can understand the information.
- Penetration testing (pen testing): A practice that uses hacker tools and techniques as a way to discover and evaluate security flaws. It is essentially a simulated cyberattack to check for exploitable vulnerabilities.
- Social engineering: A technique that uses psychological manipulation to trick users into making security mistakes or giving away sensitive information. When individuals are targeted, hackers are usually trying to trick people into giving them passwords or bank information. Examples include deceptive emails or text messages with the promise of a reward.
- Threat actor: The person behind the event. This could be an external threat who launches a phishing campaign or an employee who accidentally leaves sensitive documents on their desk.
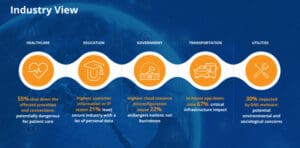
- External threat: An external threat is an attack by a hacker not associated with the affected institution, where no trust or privilege previously existed. In the education sector, 80% of cybersecurity incidents were from external threats. In healthcare, 61% of threat actors are external.
- Internal threat: An internal threat is a threat actor within the organization. In the education sector, 20% of cybersecurity incidents were from internal threats. In healthcare, that number is significantly higher at 39%.
- Incident: A security event that compromises the integrity, confidentiality or availability of an information asset.
- Data breach: An incident that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party.
The Most Common Types of Cyberattacks
Below is a breakdown of the 10 most common types of cyberattacks, according to Infocyte.
Malware
Malware, which is a catch-all term and short for “malicious software,” uses a vulnerability to breach a network when a user clicks a dangerous link or email attachment, which is then used to install malicious software inside the system. Malware can do many things, including deny access to the critical components of a network, obtain information by retrieving data from the hard drive, and even render a system inoperable.
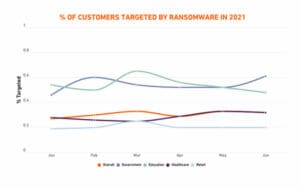
Ransomware, which is a type of malware that denies access to data and threatens to publish or delete it unless a ransom is paid, has significantly impacted schools and hospitals in recent months. In the first six months of 2021, globally, the education sector saw a 615% spike in ransomware incidents compared to 151% across all sectors, according to a study from SonicWall. The healthcare sector saw a 594% increase. In three out of six months during the first half of 2021, education customers saw even more ransomware attempts than government customers.
Most law enforcement agencies try to discourage compromised organizations from paying a ransom because it funds malicious groups. The FBI says organizations should not pay a ransom because it doesn’t guarantee that you’ll get data back and it encourages more ransomware activities.
However, a recent survey has found that 83% of ransomware victims give in to their attackers’ demands, and nearly two out of three organizations were victims in the past year.
Tragically, an Alabama mother is suing Springhill Medical Center after she says her baby received botched care and later died while the hospital was dealing with a ransomware attack. According to the Wallstreet Journal, the lawsuit is the first credible public claim that someone’s death was caused at least in part by hackers. This is just one example of the possible threat posed by a lack of solid cybersecurity practices.
Phishing
Phishing attacks masquerade as legitimate requests for information through email and trick users into revealing account credentials or other information. Some attackers leverage fake domains that are similar to legitimate websites in an attempt to capture credentials. The emails often appear to be legitimate but link the recipient to a malicious file or script designed to give hackers access to the device and take control.
Phishing attacks can also take place through phone calls (voice phishing), text messages (SMS phishing), or on social media networks through direct messages.
Man-in-the-Middle (MitM) Attacks
These attacks occur when a hacker intercepts the communication between two parties in an attempt to spy on the victims, steal personal information or credentials, or alter the conversation in some way.
According to Lepide, MitM attacks are less common these days as most email and chat systems use end-to-end encryption which prevents third parties from tampering with data that is transmitted across the network, regardless of whether the network is secure or not. This type of attack often exploits unsecured public WiFi networks.
Phishing or malware attacks are often leveraged to carry out a MitM attack, says Infocyte.
Denial-of-Service (DoS)/Distributed Denial of Service (DDoS) Attacks
DoS attacks work by flooding systems, servers and/or networks with traffic to overload resources and bandwidth, potentially resulting in the system being unable to process and fulfill legitimate service requests. Most sophisticated firewalls are able to detect and respond to DoS attacks.
However, DDoS attacks are launched from several infected devices with the goal of achieving service denial and taking a system offline, making way for another attack to enter the network/environment. In Oct. 2020, a DDoS attack paralyzed the Miami-Dade County Public School’s e-learning platform.
A 2020 joint report from DNS security firm EfficientIP and International Data Corp found four out of five companies experienced a DNS attack, with traditional DDoS making up 27% of the attacks (39% experienced phishing attempts and 34% experienced malware-based attacks).
In 2019, a man was sentenced to 10 years in prison and ordered to pay $443,000 for launching a DDoS attack against several U.S children’s hospitals in 2014. Authorities said the hackers knocked Boston Children’s Hospital offline for days, disrupting the day-to-day operations and research capabilities.
Internet of Things (IoT) Attacks
The Internet of Things (IoT) is a network of Internet-connected objects able to collect and exchange data, such as IP phones, printers, intercom systems, and security cameras. IoT devices are generally less secure than most modern operating systems, making them a big target for hackers. The interconnectedness of IoT devices makes it possible for hackers to breach an entry point and use it as a gate to exploit other devices in the network.
More than 30% of all network-connected endpoints are IoT devices, and a 2019 Gartner report found the adoption of enterprise IoT grew 21.5% from 2018 to 2019, totaling an estimated 4.8 billion devices.
A 2020 report from Unit 42, a threat intelligence team at Palo Alto Networks, analyzed security incidents spanning 1.2 million IoT devices in thousands of locations across enterprise IT and healthcare organizations in the U.S. The analysis found that “the general security posture of IoT devices is declining, leaving organizations vulnerable to new IoT-targeted malware as well as older attack techniques that IT teams have long forgotten.” It also found 98% of all IoT devices are unencrypted, potentially exposing personal and confidential data.
Password Attack
This is a type of cyberattack where a hacker tries to guess a user’s password. Methods used to identify an individual password include social engineering, gaining access to a password database, testing the network connection to obtain unencrypted passwords, or simply by guessing.
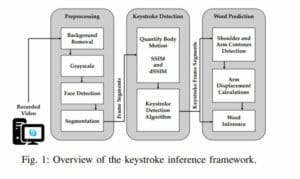
In 2020, remote work and distance learning brought on a whole host of cybersecurity issues which were compounded by the surge in the use of videoconferencing platforms like Zoom, Microsoft Teams and Google Meets. Through this surge, researchers discovered that tiny visual cues and an algorithm can be used by hackers to guess a user’s password if they sign in to an account while on a video call.
According to Forbes, citing the study, a hacker can use a methodology called keystroke inference, which is essentially watching the shoulders and upper arms for clues as to what the user at the other end of the call is typing.
It is likely we’ll see less and less of these attacks as more options become available for identity verification. According to Experian’s annual Global Identity & Fraud Report, for the first time in four years, passwords did not earn a spot in the top three most secure methods for authenticating a customer’s identity. This is especially good news since a 2020 survey from Visual Objects found Millennial workers are 6.5 times more likely to reuse work passwords than Baby Boomers, who use safer password practices.
Cybersecurity experts recommend companies integrate a two-factor authentication system or a password manager. Neither requires employees to recall complex strings of characters and both better protect data.
Server Query Language (SQL) Injections
SQL injections occur when an attacker inserts malicious code into a service using SQL language, forcing the server to deliver protected information. It usually involves submitting malicious code into an unprotected website comment section or search box.
SQL databases use SQL statements to query data, and these statements are typically executed through an HTML form on a webpage, according to Lepide. If the database permissions have not been set properly, the attacker may be able to exploit the HTML form to execute queries that will create, read, modify or delete the data stored in the database.
Cross-Site Scripting (XSS) Attacks
These attacks are similar to SQL injection attacks except instead of extracting data from a database, they are usually meant to infect other users who visit the site. Using the example of the comments section on a webpage, Lepide says if the user input isn’t filtered before the comment is published, an attacker can publish a malicious script that is hidden on the page. When the user visits the page, the script can infect their device or be used to extract the user’s credentials. The attackers could also redirect the user to a malicious website.
Zero-Day Exploit
In these cyberattacks, hackers learn of a new vulnerability in a widely-used software program or operating system and then target organizations who use that software to exploit the vulnerability before a fix becomes available.
Rootkits
Rootkits are installed inside legitimate software and enable attackers to gain remote control and administration-level access over a system. Infocyte says since rootkits hide in legitimate software, once a user allows the program to make changes to their operating system, the rootkit installs itself in the system and remains dormant until the attacker activates it or it is triggered through a persistence mechanism.
Rootkits are typically spread through email attachments or downloads from insecure websites.
Improving Cybersecurity for Your Next Project
It is clear that cyberattacks are a real threat to vertical markets such as hospitals, K-12 school districts and colleges campuses, and have been worsened by the pandemic. Strong cybersecurity practices are a must-have to truly ensure the safety and security of all students, patients, and employees.
Here are some resources that emphasize the importance of cybersecurity:
- An Integrator’s Role in Making Schools Safe
- Better Cybersecurity Standards Mean Better Physical Security
- Why Cybersecurity Is Such a Wise Investment
- Are Campuses Really Ready to Embrace the Cloud, AI and Cybersecurity?
- The Convergence of Physical and Cyber Security in Healthcare: How to Minimize Threats
- HHS Releases Healthcare Cybersecurity Best Practices
- Your Guide to Implementing a Zero Trust Network Architecture
- Remote Learning and Cyber Risk: Educators Must Address Security Concerns
- Three Attack Methods You Need to Protect Against in 2021 And Beyond
- Increase Your Defenses Against Cyber Attacks Now
- How to Hire the Right IT Employee
And for IT and cybersecurity employees who may have their work cut out for them, here are some ways to help avoid burnout.